Introduction
Generate ECC Private Key. We will be generating a private key using the prime256v1 ECC curve. Openssl ecparam -out private.key -name prime256v1 -genkey Generate Certificate Request. Now, use OpenSSL to generate a CSR (Certificate Signing Request) for signing the certificate. We will generate the CSR with 512-bit SHA2.
The example 'C' program eckeycreate.c demonstrates how to generate elliptic curve cryptography (ECC) key pairs, using the OpenSSL library functions.
- Oct 31, 2016 My scenario is generate key pair using openSSL, sign with openSSL & do verification with micro-ecc. Can you please share if you have any sample code for this? My confusion was how we can convert key structure of openSSL to suit as input to.
- Openssl ecparam -genkey -name prime256v1 -noout -out ecprivate.pem openssl ec -in ecprivate.pem -pubout -out ecpublic.pem This created 2 files ecprivate.pem and ecpublic.pem. I want to create a.pfx file using this pair. I use the command below. Openssl pkcs12 -export -inkey ecprivate.pem -in ecpublic.pem -out ec.pfx So here is the.
Example Code Listing
Compiling the Code
Compile the test program with:
Example Output
The program will create and display a new elliptic curve cryptography (ECC) key pair, similar to the output shown below:
Remarks
Note: The list of possible ECC key types (curves) can be shown using the command openssl ecparam -list_curves.
Generate ssh key mac for gitlab. Using ECC keys for certificate generation can also be seen and tested in WebCert.
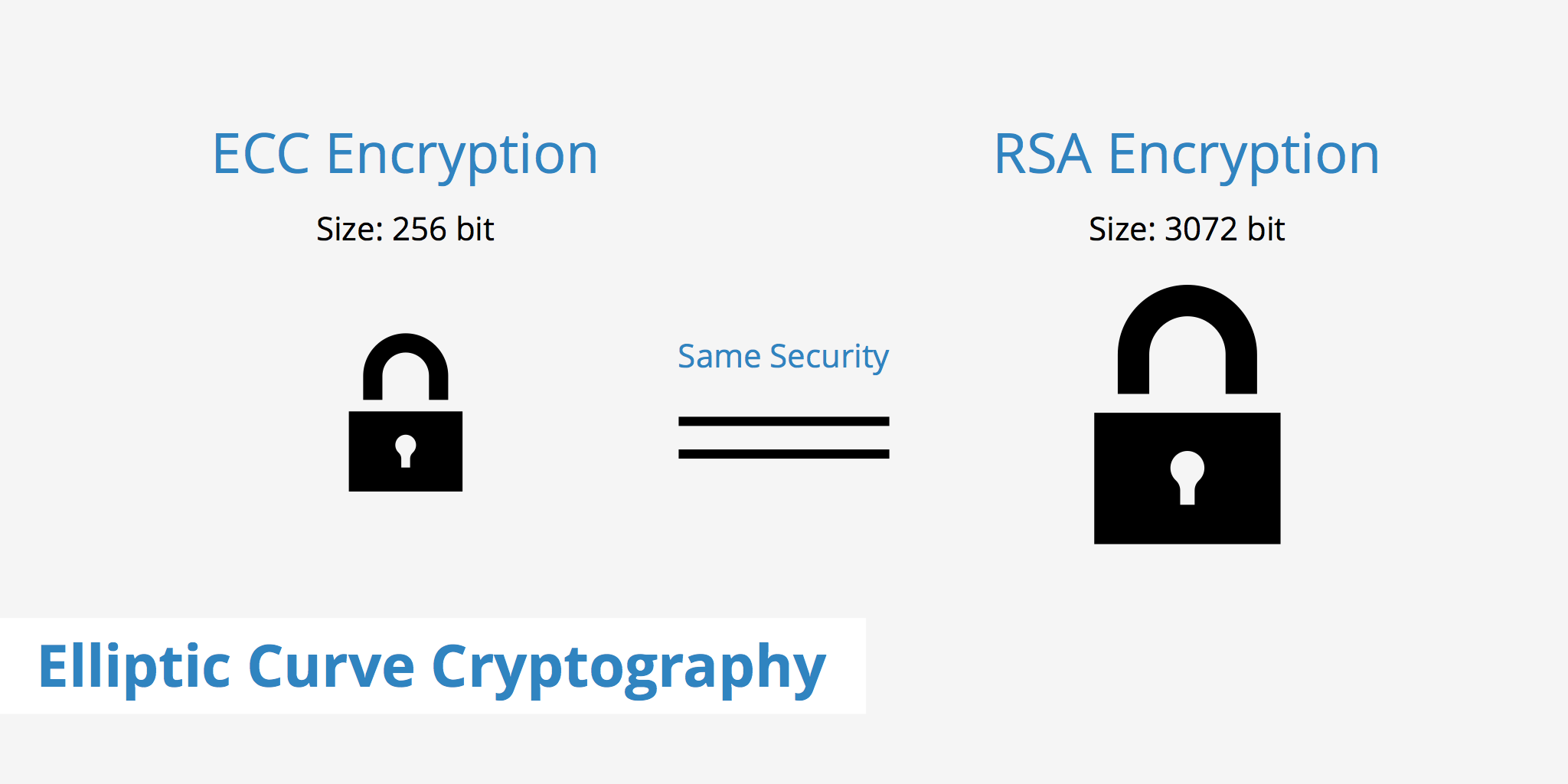
How to generate keys in PEM formatusing the OpenSSL command line tools?
RSA keys
Generate Ecc Key Pair Openssl
The JOSE standard recommends a minimum RSA key size of 2048 bits.
To generate a 2048-bit RSA private + public key pair for use in RSxxx and PSxxxsignatures:
Elliptic Curve keys
To generate an EC key pair the curve designation must be specified. Note thatJOSE ESxxx signatures require P-256, P-384 and P-521 curves (see theircorresponding OpenSSL identifiers below).
Elliptic Curve private + public key pair for use with ES256 signatures:
Elliptic Curve private + public key pair for use with ES384 signatures:
Elliptic Curve private + public key pair for use with ES512 signatures:
PEM key parsing in Java
The BouncyCastle library provides a simpleutility to parse PEM-encoded keys in Java, to use them for JWS or JWE later.
Openssl Generate Ecc Key Pair 1
For Maven you should include the following BouncyCastle dependencies (where1.52 is the latest stable version as of May 2015):
Openssl Generate Ecc Key Pair Key
Example parsing of an PEM-encoded EC key in Java:
Most Viewed News
- ✔ Free Cd Key Generator For Steam
- ✔ Games For Windows Live Product Key Generator Download
- ✔ Microsoft Windows 7 Professional Product Key Generator
- ✔ Key Generation For Tweet Id
- ✔ Csgo Product Key Generator Download
- ✔ Avs Video Editor 7.0 Activation Key Generator
- ✔ Nero Burning Rom Key Generator
- ✔ Office 2010 Product Key Online Generator
- ✔ Euro Truck Simulator 1.3 Key Generator